Microsoft Network Adapter Multiplexor Enable
An alternative is to right click Disable & Enable on the LBFO team interface. Each underlying NIC does not have to be restarted because they reset when you apply the jumbo frame setting. Since the LBFO adapter never understands it needs to reset to apply the MTU change, it must be done manually.
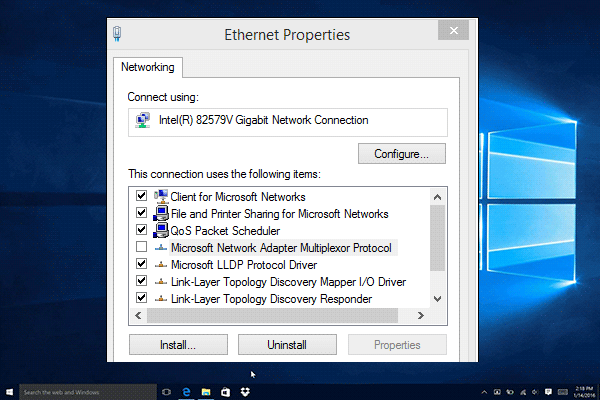
- Jun 14, 2020 Client for Microsoft Networks File and Printer Sharing for Microsoft Networks QoS Packet Scheduler x Internet Protocol Version 4 (TCP/IPv4) Link-Layer Topology Discovery Mapper I/O Driver Microsoft Network Adapter Multiplexor Protocol Microsoft LLDP Protocol Driver Internet Protocol Version 6 (TCP/IPv6.
- Microsoft Network Adapter Multiplexor Protocol - Windows 10 Service. Microsoft Network Adapter Multiplexor Protocol. This service also exists in Windows 8. Startup Type.
- How to Enable or Disable Network Adapters in Windows A network adapter is a computer hardware component that connects a computer to a computer network known as a network connection. This tutorial will show you different ways to enable or disable a network adapter (NIC) or network connections in Windows 7, Windows 8, and Windows 10.
Applies to: Windows Server (Semi-Annual Channel), Windows Server 2016
Jan 11, 2017 You can't use the windows driver for teaming because doesn't contain multiplexer protocol. Proposed as answer by Cartman Shen Microsoft contingent staff Wednesday, January 11, 2017 3:38 AM Friday, December 30, 2016 7:53 AM. Mar 05, 2020 Should I Enable the Microsoft Network Adapter Multiplexor Protocol? As I mentioned before, the Protocol only works when teaming or combining multiple Network Adapters. If you try to enable this option by selecting the option manually while the other items in the list are enabled, you will see this error.
In this topic, we provide you with instructions to deploy Converged NIC in a Teamed NIC configuration with Switch Embedded Teaming (SET).
The example configuration in this topic describes two Hyper-V hosts, Hyper-V Host 1 and Hyper-V Host 2. Both hosts have two network adapters. On each host, one adapter is connected to the 192.168.1.x/24 subnet, and one adapter is connected to the 192.168.2.x/24 subnet.
Step 1. Test the connectivity between source and destination
Ensure that the physical NIC can connect to the destination host. This test demonstrates connectivity by using Layer 3 (L3) - or the IP layer - as well as the Layer 2 (L2) virtual local area networks (VLAN).
View the first network adapter properties.
Results:
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed Test-40G-1 Mellanox ConnectX-3 Pro Ethernet Adapter 11 Up E4-1D-2D-07-43-D0 40 Gbps View additional properties for the first adapter, including the IP address.
Results:
Parameter Value IPAddress 192.168.1.3 InterfaceIndex 11 InterfaceAlias Test-40G-1 AddressFamily IPv4 Type Unicast PrefixLength 24 View the second network adapter properties.
Results:
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed TEST-40G-2 Mellanox ConnectX-3 Pro Ethernet A..#2 13 Up E4-1D-2D-07-40-70 40 Gbps View additional properties for the second adapter, including the IP address.
Results:
Parameter Value IPAddress 192.168.2.3 InterfaceIndex 13 InterfaceAlias TEST-40G-2 AddressFamily IPv4 Type Unicast PrefixLength 24 Verify that other NIC Team or SET member pNICs has a valid IP address.
Use a separate subnet, (xxx.xxx.2.xxx vs xxx.xxx.1.xxx), to facilitate sending from this adapter to the destination. Otherwise, if you locate both pNICs on the same subnet, the Windows TCP/IP stack load balances among the interfaces and simple validation becomes more complicated.
Step 2. Ensure that source and destination can communicate
In this step, we use the Test-NetConnection Windows PowerShell command, but if you can use the ping command if you prefer.
Verify bi-directional communication.
Results:
Parameter Value ComputerName 192.168.1.5 RemoteAddress 192.168.1.5 InterfaceAlias Test-40G-1 SourceAddress 192.168.1.3 PingSucceeded False PingReplyDetails (RTT) 0 ms In some cases, you might need to disable Windows Firewall with Advanced Security to successfully perform this test. If you disable the firewall, keep security in mind and ensure that your configuration meets your organization's security requirements.
Disable all firewall profiles.
After disabling the firewall profiles, test the connection again.
Results:
Parameter Value ComputerName 192.168.1.5 RemoteAddress 192.168.1.5 InterfaceAlias Test-40G-1 SourceAddress 192.168.1.3 PingSucceeded False PingReplyDetails (RTT) 0 ms Verify the connectivity for additional NICs. Repeat the previous steps for all subsequent pNICs included in the NIC or SET team.
Results:
Parameter Value ComputerName 192.168.2.5 RemoteAddress 192.168.2.5 InterfaceAlias Test-40G-2 SourceAddress 192.168.2.3 PingSucceeded False PingReplyDetails (RTT) 0 ms
Step 3. Configure the VLAN IDs for NICs installed in your Hyper-V hosts
Many network configurations make use of VLANs, and if you are planning to use VLANs in your network, you must repeat the previous test with VLANs configured.
For this step, the NICs are in ACCESS mode. However, when you create a Hyper-V Virtual Switch (vSwitch) later in this guide, the VLAN properties are applied at the vSwitch port level.
Because a switch can host multiple VLANs, it is necessary for the Top of Rack (ToR) physical switch to have the port that the host is connected to configured in Trunk mode.
Note
Consult your ToR switch documentation for instructions on how to configure Trunk mode on the switch.
The following image shows two Hyper-V hosts with two network adapters each that have VLAN 101 and VLAN 102 configured in network adapter properties.
Microsoft Network Adapter Driver
Tip
According to the Institute of Electrical and Electronics Engineers (IEEE) networking standards, the Quality of Service (QoS) properties in the physical NIC act on the 802.1p header that is embedded within the 802.1Q (VLAN) header when you configure the VLAN ID.
Configure the VLAN ID on the first NIC, Test-40G-1.
Results:
Name DisplayName DisplayValue RegistryKeyword RegistryValue TEST-40G-1 VLAN ID 101 VlanID {101} Restart the network adapter to apply the VLAN ID.
Ensure the Status is Up.
Results:
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed Test-40G-1 Mellanox ConnectX-3 Pro Ethernet Ada.. 11 Up E4-1D-2D-07-43-D0 40 Gbps Configure the VLAN ID on the second NIC, Test-40G-2.
Results:
Name DisplayName DisplayValue RegistryKeyword RegistryValue TEST-40G-2 VLAN ID 102 VlanID {102} Restart the network adapter to apply the VLAN ID.
Ensure the Status is Up.
Results:
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed Test-40G-2 Mellanox ConnectX-3 Pro Ethernet Ada.. 11 Up E4-1D-2D-07-43-D1 40 Gbps Important
It might take several seconds for the device to restart and become available on the network.
Verify the connectivity for the first NIC, Test-40G-1.
If connectivity fails, inspect the switch VLAN configuration or destination participation in the same VLAN.
Results:
Parameter Value ComputerName 192.168.1.5 RemoteAddress 192.168.1.5 InterfaceAlias Test-40G-1 SourceAddress 192.168.1.5 PingSucceeded True PingReplyDetails (RTT) 0 ms Verify the connectivity for the first NIC, Test-40G-2.
If connectivity fails, inspect the switch VLAN configuration or destination participation in the same VLAN.
Results:
Parameter Value ComputerName 192.168.2.5 RemoteAddress 192.168.2.5 InterfaceAlias Test-40G-2 SourceAddress 192.168.2.3 PingSucceeded True PingReplyDetails (RTT) 0 ms Important
It's not uncommon for a Test-NetConnection or ping failure to occur immediately after you perform Restart-NetAdapter. So wait for the network adapter to fully initialize, and then try again.
If the VLAN 101 connections work, but the VLAN 102 connections don't, the problem might be that the switch needs to be configured to allow port traffic on the desired VLAN. You can check for this by temporarily setting the failing adapters to VLAN 101, and repeating the connectivity test.
The following image shows your Hyper-V hosts after successfully configuring VLANs.
Step 4. Configure Quality of Service (QoS)
Note
You must perform all of the following DCB and QoS configuration steps on all hosts that are intended to communicate with each other.
Install Data Center Bridging (DCB) on each of your Hyper-V hosts.
- Optional for network configurations that use iWarp.
- Required for network configurations that use RoCE (any version) for RDMA services.
Results:
Success Restart Needed Exit Code Feature Result True No Success {Data Center Bridging} Set the QoS policies for SMB-Direct:
- Optional for network configurations that use iWarp.
- Required for network configurations that use RoCE (any version) for RDMA services.
In the example command below, the value “3” is arbitrary. You can use any value between 1 and 7 as long as you consistently use the same value throughout the configuration of QoS policies.
Results:
Parameter Value Name SMB Owner Group Policy (Machine) NetworkProfile All Precedence 127 JobObject NetDirectPort 445 PriorityValue 3 Set additional QoS policies for other traffic on the interface.
Rumors, leaks, announcements, fan art, and everything in between are allowed, as long as it's directly related to Fallout 4. A place for any and all discussion about Fallout 4. We currently have megathreads for:. Fallout 4 large address aware. See the rules below for more information.System requirements. Official and Un-Official can be foundFallout Network Discord serverThe invite link can be found.POSTING GUIDELINES.Before posting anything to the subreddit, check our to see if a megathread exists.
Results:
Parameter Value Name DEFAULT Owner Group Policy (Machine) NetworkProfile All Precedence 127 Template Default JobObject PriorityValue 0 Turn on Priority Flow Control for SMB traffic, which is not required for iWarp.
Results:
Priority Enabled PolicySet IfIndex IfAlias 0 False Global 1 False Global 2 False Global 3 True Global 4 False Global 5 False Global 6 False Global 7 False Global IMPORTANTIf your results do not match these results because items other than 3 have an Enabled value of True, you must disable FlowControl for these classes.
Under more complex configurations, the other traffic classes might require flow control, however these scenarios are outside the scope of this guide.
Enable QoS for the first NIC, Test-40G-1.
Capabilities:
Parameter Hardware Current MacSecBypass NotSupported NotSupported DcbxSupport None None NumTCs(Max/ETS/PFC) 8/8/8 8/8/8 OperationalTrafficClasses:
TC TSA Bandwidth Priorities 0 Strict 0-7 OperationalFlowControl:
Priority 3 Enabled
OperationalClassifications:
Protocol Port/Type Priority Default 0 NetDirect 445 3 Enable QoS for the second NIC, Test-40G-2.
Capabilities:
Parameter Hardware Current MacSecBypass NotSupported NotSupported DcbxSupport None None NumTCs(Max/ETS/PFC) 8/8/8 8/8/8 OperationalTrafficClasses:
TC TSA Bandwidth Priorities 0 Strict 0-7 OperationalFlowControl:
Priority 3 Enabled
OperationalClassifications:
Protocol Port/Type Priority Default 0 NetDirect 445 3 Reserve half the bandwidth to SMB Direct (RDMA)
Results:
Name Algorithm Bandwidth(%) Priority PolicySet IfIndex IfAlias SMB ETS 50 3 Global View the bandwidth reservation settings:
Results:
Name Algorithm Bandwidth(%) Priority PolicySet IfIndex IfAlias [Default] ETS 50 0-2,4-7 Global SMB ETS 50 3 Global (Optional) Create two additional traffic classes for tenant IP traffic.
Results:
Name Algorithm Bandwidth(%) Priority PolicySet IfIndex IfAlias IP1 ETS 10 1 Global Results:
Name Algorithm Bandwidth(%) Priority PolicySet IfIndex IfAlias IP2 ETS 10 2 Global View the QoS traffic classes.
Results:
Name Algorithm Bandwidth(%) Priority PolicySet IfIndex IfAlias [Default] ETS 30 0,4-7 Global SMB ETS 50 3 Global IP1 ETS 10 1 Global IP2 ETS 10 2 Global (Optional) Override the debugger.
By default, the attached debugger blocks NetQos.
Results:
Step 5. Verify the RDMA configuration (Mode 1)
You want to ensure that the fabric is configured correctly prior to creating a vSwitch and transitioning to RDMA (Mode 2).
The following image shows the current state of the Hyper-V hosts.
Verify the RDMA configuration.
Results:
Name InterfaceDescription Enabled TEST-40G-1 Mellanox ConnectX-4 VPI Adapter #2 True TEST-40G-2 Mellanox ConnectX-4 VPI Adapter True Determine the ifIndex value of your target adapters.
You use this value in subsequent steps when you run the script you download.
Results:
InterfaceAlias InterfaceIndex IPv4Address TEST-40G-1 14 {192.168.1.3} TEST-40G-2 13 {192.168.2.3} Download the DiskSpd.exe utility and extract it into C:TEST.
Download the Test-RDMA PowerShell script to a test folder on your local drive, for example, C:TEST.
Run the Test-Rdma.ps1 PowerShell script to pass the ifIndex value to the script, along with the IP address of the first remote adapter on the same VLAN.
In this example, the script passes the ifIndex value of 14 on the remote network adapter IP address 192.168.1.5.
Results:
Note
If the RDMA traffic fails, for the RoCE case specifically, consult your ToR Switch configuration for proper PFC/ETS settings that should match the Host settings. Refer to the QoS section in this document for reference values.
Run the Test-Rdma.ps1 PowerShell script to pass the ifIndex value to the script, along with the IP address of the second remote adapter on the same VLAN.
In this example, the script passes the ifIndex value of 13 on the remote network adapter IP address 192.168.2.5.
Results:
Step 6. Create a Hyper-V vSwitch on your Hyper-V hosts
The following image shows Hyper-V Host 1 with a vSwitch.
Create a vSwitch in SET mode on Hyper-V host 1.
Result:
Name SwitchType NetAdapterInterfaceDescription VMSTEST External Teamed-Interface View the physical adapter team in SET.
Results:
Display two views of the host vNIC
Results:
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed vEthernet (VMSTEST) Hyper-V Virtual Ethernet Adapter #2 28 Up E4-1D-2D-07-40-71 80 Gbps View additional properties of the host vNIC.
Results:
Name IsManagementOs VMName SwitchName MacAddress Status IPAddresses VMSTEST True VMSTEST E41D2D074071 {Ok} Test the network connection to the remote VLAN 101 adapter.
Results:
Step 7. Remove the Access VLAN setting
In this step, you remove the ACCESS VLAN setting from the physical NIC and to set the VLANID using the vSwitch.
You must remove the ACCESS VLAN setting to prevent both auto-tagging the egress traffic with the incorrect VLAN ID and from filtering ingress traffic which doesn't match the ACCESS VLAN ID.
Remove the setting.
Set the VLAN ID.
Results:
Test the network connection.
Results:
IMPORTANT If your results are not similar to the example results and ping fails with the message 'WARNING: Ping to 192.168.1.5 failed -- Status: DestinationHostUnreachable,' confirm that the “vEthernet (VMSTEST)” has the proper IP address.
If the IP address is not set, correct the issue.
Rename the Management NIC.
Results:
Name IsManagementOs VMName SwitchName MacAddress Status IPAddresses CORP-External-Switch True CORP-External-Switch 001B785768AA {Ok} MGT True VMSTEST E41D2D074071 {Ok} View additional NIC properties.
Results:
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed vEthernet (MGT) Hyper-V Virtual Ethernet Adapter #2 28 Up E4-1D-2D-07-40-71 80 Gbps
Step 8. Test Hyper-V vSwitch RDMA
The following image shows the current state of your Hyper-V hosts, including the vSwitch on Hyper-V Host 1.
Set the priority tagging on the Host vNIC to complement the previous VLAN settings.
Results:
Name : MGTIeeePriorityTag : On
Create two host vNICs for RDMA and connect them to the vSwitch VMSTEST.
View the Management NIC properties.
Results:
Name IsManagementOs VMName SwitchName MacAddress Status IPAddresses CORP-External-Switch True CORP-External-Switch 001B785768AA {Ok} Mgt True VMSTEST E41D2D074071 {Ok} SMB1 True VMSTEST 00155D30AA00 {Ok} SMB2 True VMSTEST 00155D30AA01 {Ok}
Step 9. Assign an IP address to the SMB Host vNICs vEthernet (SMB1) and vEthernet (SMB2)
The TEST-40G-1 and TEST-40G-2 physical adapters still have an ACCESS VLAN of 101 and 102 configured. Because of this, the adapters tag the traffic - and ping succeeds. Previously, you configured both pNIC VLAN IDs to zero, then set the VMSTEST vSwitch to VLAN 101. After that, you were still able to ping the remote VLAN 101 adapter by using the MGT vNIC, but there are currently no VLAN 102 members.
Remove the ACCESS VLAN setting from the physical NIC to prevent it from both auto-tagging the egress traffic with the incorrect VLAN ID and to prevent it from filtering ingress traffic that doesn't match the ACCESS VLAN ID.
Results:
Test the remote VLAN 102 adapter.
Results:
Add a new IP address for interface vEthernet (SMB2).
Results:
Test the connection again.
Place the RDMA Host vNICs on the pre-existing VLAN 102.
Results:
Inspect the mapping of SMB1 and SMB2 to the underlying physical NICs under the vSwitch SET Team.
The association of Host vNIC to Physical NICs is random and subject to rebalancing during creation and destruction. In this circumstance, you can use an indirect mechanism to check the current association. The MAC addresses of SMB1 and SMB2 are associated with the NIC Team member TEST-40G-2. This is not ideal because Test-40G-1 does not have an associated SMB Host vNIC, and will not allow for utilization of RDMA traffic over the link until an SMB Host vNIC is mapped to it.
Results:
View the VM network adapter properties.
Results:
View the network adapter team mapping.
The results should not return information because you have not yet performed mapping.
Map SMB1 and SMB2 to separate physical NIC team members, and to view the results of your actions.
Important
Ensure that you complete this step before proceeding, or your implementation fails.
Results:
Confirm the MAC associations created previously.
Results:
Test the connection from the remote system because both Host vNICs reside on the same subnet and have the same VLAN ID (102).
Results:
Results:
Set the name, switch name, and priority tags.
Results:
View the vEthernet network adapter properties.
Results:
Enable the vEthernet network adapters.
Results:
Step 10. Validate the RDMA functionality
You want to validate the RDMA functionality from the remote system to the local system, which has a vSwitch, to both members of the vSwitch SET team.
Because both Host vNICs (SMB1 and SMB2) are assigned to VLAN 102, you can select the VLAN 102 adapter on the remote system.
In this example, the NIC Test-40G-2 does RDMA to SMB1 (192.168.2.111) and SMB2 (192.168.2.222).
Can' T Enable Microsoft Network Adapter Multiplexor Protocol Windows 10
Tip
Can' T Enable Microsoft Network Adapter Multiplexor Protocol Software
You might need to disable the Firewall on this system. Consult your fabric policy for details.
Results:
View the network adapter properties.
Results:
View the network adapter RDMA information.
Results:
Perform the RDMA traffic test on the first physical adapter.
Results:
Perform the RDMA traffic test on the second physical adapter.
Results:
Test for RDMA traffic from the local to the remote computer.
Results:
Perform the RDMA traffic test on the first virtual adapter.
Results:
Perform the RDMA traffic test on the second virtual adapter.
Results:
Can' T Enable Microsoft Network Adapter Multiplexor Protocol For Mac
The final line in this output, 'RDMA traffic test SUCCESSFUL: RDMA traffic was sent to 192.168.2.5,' shows that you have successfully configured Converged NIC on your adapter.
Related topics
-->Applies to: Windows Server (Semi-Annual Channel), Windows Server 2016
In this topic, we provide you with instructions to deploy Converged NIC in a Teamed NIC configuration with Switch Embedded Teaming (SET).
The example configuration in this topic describes two Hyper-V hosts, Hyper-V Host 1 and Hyper-V Host 2. Both hosts have two network adapters. On each host, one adapter is connected to the 192.168.1.x/24 subnet, and one adapter is connected to the 192.168.2.x/24 subnet.
Jul 25, 2017 The first scenario is called adapter teaming, which means using two or more adapters at the same time, so that you can send and receive more packets than a single adapter could. The second scenario is called adapter failover/high availability, where a standby adapter takes over the network connection if the primary fails.
- Tech support scams are an industry-wide issue where scammers trick you into paying for unnecessary technical support services. You can help protect yourself from scammers by verifying that the contact is a Microsoft Agent or Microsoft Employee and that the phone number is an official Microsoft global customer service number.
- Dec 21, 2016 Verify your account to enable IT peers to see that you are a professional. Dec 21, 2016 at 14:49 UTC. You use Server Manager to create the team, and then in Hyper-V the external switch network should show you a adapter called 'Microsoft Network Adapter Multiplexor Driver', which is the teamed virtual adapter.
- Feb 07, 2020 How to Enable or Disable Network Adapters in Windows A network adapter is a computer hardware component that connects a computer to a computer network known as a network connection. This tutorial will show you different ways to enable or disable a network.
- Jun 23, 2019 The Microsoft Network Adapter Multiplexor Protocol is listed in the “Items this connection uses” list for the Wifi Properties.This option is disabled for many people by default and it often gets them confused if disabling or enabling it has an effect on their connection or bandwidth. Actually enabling this protocol while the rest of the options in the list are enabled is not possible.
Step 1. Test the connectivity between source and destination
Ensure that the physical NIC can connect to the destination host. This test demonstrates connectivity by using Layer 3 (L3) - or the IP layer - as well as the Layer 2 (L2) virtual local area networks (VLAN).
View the first network adapter properties.
Results:
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed Test-40G-1 Mellanox ConnectX-3 Pro Ethernet Adapter 11 Up E4-1D-2D-07-43-D0 40 Gbps View additional properties for the first adapter, including the IP address.
Results:
Parameter Value IPAddress 192.168.1.3 InterfaceIndex 11 InterfaceAlias Test-40G-1 AddressFamily IPv4 Type Unicast PrefixLength 24 View the second network adapter properties.
Results:
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed TEST-40G-2 Mellanox ConnectX-3 Pro Ethernet A..#2 13 Up E4-1D-2D-07-40-70 40 Gbps View additional properties for the second adapter, including the IP address.
Results:
Parameter Value IPAddress 192.168.2.3 InterfaceIndex 13 InterfaceAlias TEST-40G-2 AddressFamily IPv4 Type Unicast PrefixLength 24 Verify that other NIC Team or SET member pNICs has a valid IP address.
Use a separate subnet, (xxx.xxx.2.xxx vs xxx.xxx.1.xxx), to facilitate sending from this adapter to the destination. Otherwise, if you locate both pNICs on the same subnet, the Windows TCP/IP stack load balances among the interfaces and simple validation becomes more complicated.
Step 2. Ensure that source and destination can communicate
In this step, we use the Test-NetConnection Windows PowerShell command, but if you can use the ping command if you prefer.
Verify bi-directional communication.
Results:
Parameter Value ComputerName 192.168.1.5 RemoteAddress 192.168.1.5 InterfaceAlias Test-40G-1 SourceAddress 192.168.1.3 PingSucceeded False PingReplyDetails (RTT) 0 ms In some cases, you might need to disable Windows Firewall with Advanced Security to successfully perform this test. If you disable the firewall, keep security in mind and ensure that your configuration meets your organization's security requirements.
Disable all firewall profiles.
After disabling the firewall profiles, test the connection again.
Results:
Parameter Value ComputerName 192.168.1.5 RemoteAddress 192.168.1.5 InterfaceAlias Test-40G-1 SourceAddress 192.168.1.3 PingSucceeded False PingReplyDetails (RTT) 0 ms Verify the connectivity for additional NICs. Repeat the previous steps for all subsequent pNICs included in the NIC or SET team.
Results:
It's only a teaser though, the full trailer is coming soon!This animated 3D feature is about 2 girls on a casual night out having lots and lots of fun together One of the girls has a big secret!It took 10+ months to create this animated work and it is now finally nearing completion. Worth the wait though! You may need to refresh after a while.2:37 mins long - turn up the sound!!WARNING: Does not contain nudity, but the shocking news is that one of the girls has very big breasts! Yay!Inspiration for this teaser was to create something like a movie trailer.
Parameter Value ComputerName 192.168.2.5 RemoteAddress 192.168.2.5 InterfaceAlias Test-40G-2 SourceAddress 192.168.2.3 PingSucceeded False PingReplyDetails (RTT) 0 ms
Step 3. Configure the VLAN IDs for NICs installed in your Hyper-V hosts
Many network configurations make use of VLANs, and if you are planning to use VLANs in your network, you must repeat the previous test with VLANs configured.
For this step, the NICs are in ACCESS mode. However, when you create a Hyper-V Virtual Switch (vSwitch) later in this guide, the VLAN properties are applied at the vSwitch port level.
Because a switch can host multiple VLANs, it is necessary for the Top of Rack (ToR) physical switch to have the port that the host is connected to configured in Trunk mode.
Note
Consult your ToR switch documentation for instructions on how to configure Trunk mode on the switch.
The following image shows two Hyper-V hosts with two network adapters each that have VLAN 101 and VLAN 102 configured in network adapter properties.
Tip
According to the Institute of Electrical and Electronics Engineers (IEEE) networking standards, the Quality of Service (QoS) properties in the physical NIC act on the 802.1p header that is embedded within the 802.1Q (VLAN) header when you configure the VLAN ID.
Configure the VLAN ID on the first NIC, Test-40G-1.
Results:
Name DisplayName DisplayValue RegistryKeyword RegistryValue TEST-40G-1 VLAN ID 101 VlanID {101} Restart the network adapter to apply the VLAN ID.
Ensure the Status is Up.
Results:
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed Test-40G-1 Mellanox ConnectX-3 Pro Ethernet Ada.. 11 Up E4-1D-2D-07-43-D0 40 Gbps Configure the VLAN ID on the second NIC, Test-40G-2.
Results:
Name DisplayName DisplayValue RegistryKeyword RegistryValue TEST-40G-2 VLAN ID 102 VlanID {102} Restart the network adapter to apply the VLAN ID.
Ensure the Status is Up.
Results:
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed Test-40G-2 Mellanox ConnectX-3 Pro Ethernet Ada.. 11 Up E4-1D-2D-07-43-D1 40 Gbps Important
It might take several seconds for the device to restart and become available on the network.
Verify the connectivity for the first NIC, Test-40G-1.
If connectivity fails, inspect the switch VLAN configuration or destination participation in the same VLAN.
Results:
Parameter Value ComputerName 192.168.1.5 RemoteAddress 192.168.1.5 InterfaceAlias Test-40G-1 SourceAddress 192.168.1.5 PingSucceeded True PingReplyDetails (RTT) 0 ms Verify the connectivity for the first NIC, Test-40G-2.
If connectivity fails, inspect the switch VLAN configuration or destination participation in the same VLAN.
Results:
Parameter Value ComputerName 192.168.2.5 RemoteAddress 192.168.2.5 InterfaceAlias Test-40G-2 SourceAddress 192.168.2.3 PingSucceeded True PingReplyDetails (RTT) 0 ms Important
It's not uncommon for a Test-NetConnection or ping failure to occur immediately after you perform Restart-NetAdapter. So wait for the network adapter to fully initialize, and then try again.
If the VLAN 101 connections work, but the VLAN 102 connections don't, the problem might be that the switch needs to be configured to allow port traffic on the desired VLAN. You can check for this by temporarily setting the failing adapters to VLAN 101, and repeating the connectivity test.
The following image shows your Hyper-V hosts after successfully configuring VLANs.
Step 4. Configure Quality of Service (QoS)
Note
You must perform all of the following DCB and QoS configuration steps on all hosts that are intended to communicate with each other.
Install Data Center Bridging (DCB) on each of your Hyper-V hosts.
- Optional for network configurations that use iWarp.
- Required for network configurations that use RoCE (any version) for RDMA services.
Results:
Success Restart Needed Exit Code Feature Result True No Success {Data Center Bridging} Set the QoS policies for SMB-Direct:
- Optional for network configurations that use iWarp.
- Required for network configurations that use RoCE (any version) for RDMA services.
In the example command below, the value “3” is arbitrary. You can use any value between 1 and 7 as long as you consistently use the same value throughout the configuration of QoS policies.
Results:
Parameter Value Name SMB Owner Group Policy (Machine) NetworkProfile All Precedence 127 JobObject NetDirectPort 445 PriorityValue 3 Set additional QoS policies for other traffic on the interface.
Results:
Parameter Value Name DEFAULT Owner Group Policy (Machine) NetworkProfile All Precedence 127 Template Default JobObject PriorityValue 0 Turn on Priority Flow Control for SMB traffic, which is not required for iWarp.
Results:
Priority Enabled PolicySet IfIndex IfAlias 0 False Global 1 False Global 2 False Global 3 True Global 4 False Global 5 False Global 6 False Global 7 False Global IMPORTANTIf your results do not match these results because items other than 3 have an Enabled value of True, you must disable FlowControl for these classes.
Under more complex configurations, the other traffic classes might require flow control, however these scenarios are outside the scope of this guide.
Enable QoS for the first NIC, Test-40G-1.
Capabilities:
Parameter Hardware Current MacSecBypass NotSupported NotSupported DcbxSupport None None NumTCs(Max/ETS/PFC) 8/8/8 8/8/8 OperationalTrafficClasses:
TC TSA Bandwidth Priorities 0 Strict 0-7 OperationalFlowControl:
Priority 3 Enabled
OperationalClassifications:
Protocol Port/Type Priority Default 0 NetDirect 445 3 Enable QoS for the second NIC, Test-40G-2.
Capabilities:
Parameter Hardware Current MacSecBypass NotSupported NotSupported DcbxSupport None None NumTCs(Max/ETS/PFC) 8/8/8 8/8/8 OperationalTrafficClasses:
TC TSA Bandwidth Priorities 0 Strict 0-7 OperationalFlowControl:
Priority 3 Enabled
OperationalClassifications:
Protocol Port/Type Priority Default 0 NetDirect 445 3 Reserve half the bandwidth to SMB Direct (RDMA)
Results:
Name Algorithm Bandwidth(%) Priority PolicySet IfIndex IfAlias SMB ETS 50 3 Global View the bandwidth reservation settings:
Results:
Name Algorithm Bandwidth(%) Priority PolicySet IfIndex IfAlias [Default] ETS 50 0-2,4-7 Global SMB ETS 50 3 Global (Optional) Create two additional traffic classes for tenant IP traffic.
Results:
Name Algorithm Bandwidth(%) Priority PolicySet IfIndex IfAlias IP1 ETS 10 1 Global Results:
Name Algorithm Bandwidth(%) Priority PolicySet IfIndex IfAlias IP2 ETS 10 2 Global View the QoS traffic classes.
Results:
Name Algorithm Bandwidth(%) Priority PolicySet IfIndex IfAlias [Default] ETS 30 0,4-7 Global SMB ETS 50 3 Global IP1 ETS 10 1 Global IP2 ETS 10 2 Global (Optional) Override the debugger.
By default, the attached debugger blocks NetQos.
Results:
Step 5. Verify the RDMA configuration (Mode 1)
You want to ensure that the fabric is configured correctly prior to creating a vSwitch and transitioning to RDMA (Mode 2).
The following image shows the current state of the Hyper-V hosts.
Verify the RDMA configuration.
Results:
Name InterfaceDescription Enabled TEST-40G-1 Mellanox ConnectX-4 VPI Adapter #2 True TEST-40G-2 Mellanox ConnectX-4 VPI Adapter True Determine the ifIndex value of your target adapters.
You use this value in subsequent steps when you run the script you download.
Results:
InterfaceAlias InterfaceIndex IPv4Address TEST-40G-1 14 {192.168.1.3} TEST-40G-2 13 {192.168.2.3} Download the DiskSpd.exe utility and extract it into C:TEST.
Download the Test-RDMA PowerShell script to a test folder on your local drive, for example, C:TEST.
Run the Test-Rdma.ps1 PowerShell script to pass the ifIndex value to the script, along with the IP address of the first remote adapter on the same VLAN.
In this example, the script passes the ifIndex value of 14 on the remote network adapter IP address 192.168.1.5.
Results:
Note
If the RDMA traffic fails, for the RoCE case specifically, consult your ToR Switch configuration for proper PFC/ETS settings that should match the Host settings. Refer to the QoS section in this document for reference values.
Contact the seller, see how you get along and with any luck, you can have the install disc you need by the end of the day.Techie yard sales/Macintosh user groupsYou’ll have to dig around and pen them into your calendar, but you’ll find what you need here plus Mac-based advice and camaraderie to boot. Mac os x 10.6.8 install disc download. CraigslistIf it’s for sale and local, you’ll find it on. Log in, check the local computer equipment listings and you should be able to find what you need, or at least someone who has a good lead on the Mac OS X CD or DVD that you suddenly found yourself needing for a project.Unlike eBay, there’s a little wiggle room for negotiation once you’ve contacted the seller via phone or email, so use this to your advantage and with any luck, they’ll come to you with the product.Like anything else with Craigslist, be on the lookout for scams, deals that seem too good to be true, and the like. Check that the seller has a reputation around or close to 100 percent before you order what you need.
Run the Test-Rdma.ps1 PowerShell script to pass the ifIndex value to the script, along with the IP address of the second remote adapter on the same VLAN.
In this example, the script passes the ifIndex value of 13 on the remote network adapter IP address 192.168.2.5.
Results:
Step 6. Create a Hyper-V vSwitch on your Hyper-V hosts
The following image shows Hyper-V Host 1 with a vSwitch.
Create a vSwitch in SET mode on Hyper-V host 1.
Result:
Name SwitchType NetAdapterInterfaceDescription VMSTEST External Teamed-Interface View the physical adapter team in SET.
Results:
Display two views of the host vNIC
Results:
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed vEthernet (VMSTEST) Hyper-V Virtual Ethernet Adapter #2 28 Up E4-1D-2D-07-40-71 80 Gbps View additional properties of the host vNIC.
Results:
Name IsManagementOs VMName SwitchName MacAddress Status IPAddresses VMSTEST True VMSTEST E41D2D074071 {Ok} Test the network connection to the remote VLAN 101 adapter.
Results:
Step 7. Remove the Access VLAN setting
In this step, you remove the ACCESS VLAN setting from the physical NIC and to set the VLANID using the vSwitch.
You must remove the ACCESS VLAN setting to prevent both auto-tagging the egress traffic with the incorrect VLAN ID and from filtering ingress traffic which doesn't match the ACCESS VLAN ID.
Remove the setting.
Set the VLAN ID.
Results:
Test the network connection.
Results:
IMPORTANT If your results are not similar to the example results and ping fails with the message 'WARNING: Ping to 192.168.1.5 failed -- Status: DestinationHostUnreachable,' confirm that the “vEthernet (VMSTEST)” has the proper IP address.
If the IP address is not set, correct the issue.
Rename the Management NIC.
Results:
Name IsManagementOs VMName SwitchName MacAddress Status IPAddresses CORP-External-Switch True CORP-External-Switch 001B785768AA {Ok} MGT True VMSTEST E41D2D074071 {Ok} View additional NIC properties.
Results:
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed vEthernet (MGT) Hyper-V Virtual Ethernet Adapter #2 28 Up E4-1D-2D-07-40-71 80 Gbps
Step 8. Test Hyper-V vSwitch RDMA
Can 26%2339 3bt Enable Microsoft Network Adapter Multiplexor Protocol Download
The following image shows the current state of your Hyper-V hosts, including the vSwitch on Hyper-V Host 1.
Set the priority tagging on the Host vNIC to complement the previous VLAN settings.
Results:
Name : MGTIeeePriorityTag : On
Create two host vNICs for RDMA and connect them to the vSwitch VMSTEST.
View the Management NIC properties.
Results:
Name IsManagementOs VMName SwitchName MacAddress Status IPAddresses CORP-External-Switch True CORP-External-Switch 001B785768AA {Ok} Mgt True VMSTEST E41D2D074071 {Ok} SMB1 True VMSTEST 00155D30AA00 {Ok} SMB2 True VMSTEST 00155D30AA01 {Ok}
Step 9. Assign an IP address to the SMB Host vNICs vEthernet (SMB1) and vEthernet (SMB2)
The TEST-40G-1 and TEST-40G-2 physical adapters still have an ACCESS VLAN of 101 and 102 configured. Because of this, the adapters tag the traffic - and ping succeeds. Previously, you configured both pNIC VLAN IDs to zero, then set the VMSTEST vSwitch to VLAN 101. After that, you were still able to ping the remote VLAN 101 adapter by using the MGT vNIC, but there are currently no VLAN 102 members.
Remove the ACCESS VLAN setting from the physical NIC to prevent it from both auto-tagging the egress traffic with the incorrect VLAN ID and to prevent it from filtering ingress traffic that doesn't match the ACCESS VLAN ID.
Results:
Test the remote VLAN 102 adapter.
Results:
Add a new IP address for interface vEthernet (SMB2).
Results:
Test the connection again.
Place the RDMA Host vNICs on the pre-existing VLAN 102.
Results:
Inspect the mapping of SMB1 and SMB2 to the underlying physical NICs under the vSwitch SET Team.
The association of Host vNIC to Physical NICs is random and subject to rebalancing during creation and destruction. In this circumstance, you can use an indirect mechanism to check the current association. The MAC addresses of SMB1 and SMB2 are associated with the NIC Team member TEST-40G-2. This is not ideal because Test-40G-1 does not have an associated SMB Host vNIC, and will not allow for utilization of RDMA traffic over the link until an SMB Host vNIC is mapped to it.
Results:
View the VM network adapter properties.
Results:
View the network adapter team mapping.
The results should not return information because you have not yet performed mapping.
Map SMB1 and SMB2 to separate physical NIC team members, and to view the results of your actions.
Important
Ensure that you complete this step before proceeding, or your implementation fails.
Results:
Confirm the MAC associations created previously.
Results:
Test the connection from the remote system because both Host vNICs reside on the same subnet and have the same VLAN ID (102).
Results:
Results:
Set the name, switch name, and priority tags.
Results:
View the vEthernet network adapter properties.
Results:
Enable the vEthernet network adapters.
Results:
Step 10. Validate the RDMA functionality
You want to validate the RDMA functionality from the remote system to the local system, which has a vSwitch, to both members of the vSwitch SET team.
Because both Host vNICs (SMB1 and SMB2) are assigned to VLAN 102, you can select the VLAN 102 adapter on the remote system.
In this example, the NIC Test-40G-2 does RDMA to SMB1 (192.168.2.111) and SMB2 (192.168.2.222).
Tip
You might need to disable the Firewall on this system. Consult your fabric policy for details.
Results:
Can' T Enable Microsoft Network Adapter Multiplexor Protocol Problems
Can' T Enable Microsoft Network Adapter Multiplexor Protocol Windows 10
View the network adapter properties.
Results:
View the network adapter RDMA information.
Results:
Perform the RDMA traffic test on the first physical adapter.
Results:
Perform the RDMA traffic test on the second physical adapter.
Results:
Test for RDMA traffic from the local to the remote computer.
Results:
Perform the RDMA traffic test on the first virtual adapter.
Results:
Perform the RDMA traffic test on the second virtual adapter.
Results:
Can' T Enable Microsoft Network Adapter Multiplexor Protocol Download
The final line in this output, 'RDMA traffic test SUCCESSFUL: RDMA traffic was sent to 192.168.2.5,' shows that you have successfully configured Converged NIC on your adapter.
Can' T Enable Microsoft Network Adapter Multiplexor Protocol For Windows 7
Microsoft Network Adapter Multiplexor Protocol Install
Related topics
